Top 10 Cybersecurity Terms to Know
In the digital age, cybersecurity is no longer a luxury but a necessity. It’s a critical aspect of any business operation, regardless of size or industry.
Understanding cybersecurity terms is the first step towards building a robust defense against cyber threats. These terms provide a foundation for comprehending the complex landscape of digital security.
This article aims to demystify the top 10 cybersecurity terms you should know. From malware to zero-day exploits, we’ll delve into the meanings and implications of these terms.
Whether you’re a small business owner, an IT manager, or a startup founder, basic cybersecurity concepts knowledge is invaluable. It equips you to make informed decisions about your IT strategies and safeguards your business assets.
So, let’s embark on this journey of understanding. Let’s equip ourselves with the knowledge to navigate the intricate world of cybersecurity.
Remember, in the realm of digital security, knowledge is your most potent weapon. We will help you learn about informational security concepts.
Understanding Cybersecurity: The Foundation of Digital Protection
Cybersecurity, at its core, is the practice of safeguarding systems, networks, personal data and programs from digital attacks and security breaches. These attacks often aim to access, change, or destroy sensitive information, disrupt business operations, or extort money from users.
Understanding cybersecurity is fundamental to protecting your digital assets. It’s about recognizing the threats that exist and implementing measures to counter them. This understanding forms the bedrock of your digital protection strategy, enabling you to secure your business in an increasingly interconnected world.
Malware: The Malicious Software Undermining Your Security
Malware, short for malicious software, is designed to harm or exploit any programmable device or network. It’s a broad term that encompasses various harmful software types, including viruses, worms, ransomware, and spyware.
Malware poses a significant threat to your cybersecurity. It can steal sensitive data, disrupt operations, or even damage your systems. Understanding malware and its various forms is crucial in developing effective defense strategies and maintaining the integrity of your digital environment.
Phishing: The Deceptive Threat to Your Personal Information
Phishing is a cybercrime where targets are contacted by email, telephone, or text message by someone posing as a legitimate institution. The aim is to lure individuals into providing sensitive data such as personally identifiable information, banking and credit card details, and passwords.
This deceptive method is a significant cybersecurity concern. It exploits the human element of security, tricking individuals into revealing confidential information. Awareness and understanding of phishing techniques are vital in protecting your personal and organizational data from these insidious attacks.
Ransomware: The Extortionist’s Tool in the Cyber Realm
Ransomware is a type of malicious software designed to block access to a computer system until a sum of money is paid. It’s a digital form of extortion where the attacker holds the victim’s data hostage.
Understanding ransomware and its mechanisms is crucial for businesses and individuals alike. It’s a potent threat that can cause significant disruption and financial loss. Awareness of this cybersecurity term can help in implementing effective strategies to prevent such attacks and safeguard your digital assets.
Botnets: The Silent Army of Compromised Computers
A botnet is a network of private computers, infected with malicious software and controlled as a group without the owners’ knowledge. These networks can be used to send spam emails, steal data, or stage DDoS attacks.
Understanding the concept of botnets is essential for IT managers and business owners. It helps in recognizing the signs of a botnet infection and taking appropriate measures to secure the network. Awareness of this cybersecurity term can significantly enhance your organization’s defense against such covert threats.
DDoS Attacks: Disrupting Services Through Overwhelming Traffic
Distributed Denial of Service, or DDoS, is a type of cyber-attack that makes a service unavailable by overwhelming it with traffic from multiple sources. The goal is to overload the system, causing it to slow down or crash, thereby denying service to legitimate users.
For businesses, understanding DDoS attacks is crucial. These attacks can disrupt operations, leading to financial losses and damage to the company’s reputation. By recognizing the signs of a DDoS attack, businesses can respond quickly, minimizing downtime and maintaining customer trust.
Encryption: The Art of Securing Data by Obscuring Information
Encryption is the process of converting information or data into a code to prevent unauthorized access. It’s a fundamental aspect of cybersecurity, used to protect sensitive data such as financial information, personal details, and business secrets.
Understanding encryption is vital for businesses of all sizes. It ensures that even if data is intercepted during transmission, it remains unreadable to anyone without the correct decryption key. This protects the integrity of the data and the privacy of individuals and businesses alike.
Firewalls: The Gatekeepers of Network Traffic
Firewalls serve as the first line of defense in network security. They monitor and filter incoming and outgoing network traffic based on an organization’s previously established security policies.
Firewalls can block unauthorized access while permitting outward communication. They are essential for controlling the flow of traffic and protecting the network from potential threats. Understanding how firewalls work can help businesses establish effective security measures and protect their digital assets.
Insider Threats: The Danger Within Your Organization
Insider threats refer to security risks that originate from within the targeted organization. These threats often come from employees or officers who have access to sensitive information.
Understanding the concept of insider threats is crucial for businesses. It helps them develop strategies to prevent unauthorized access to sensitive data and maintain the integrity of their IT systems. Awareness of insider threats can also guide the implementation of access control measures and employee training programs.
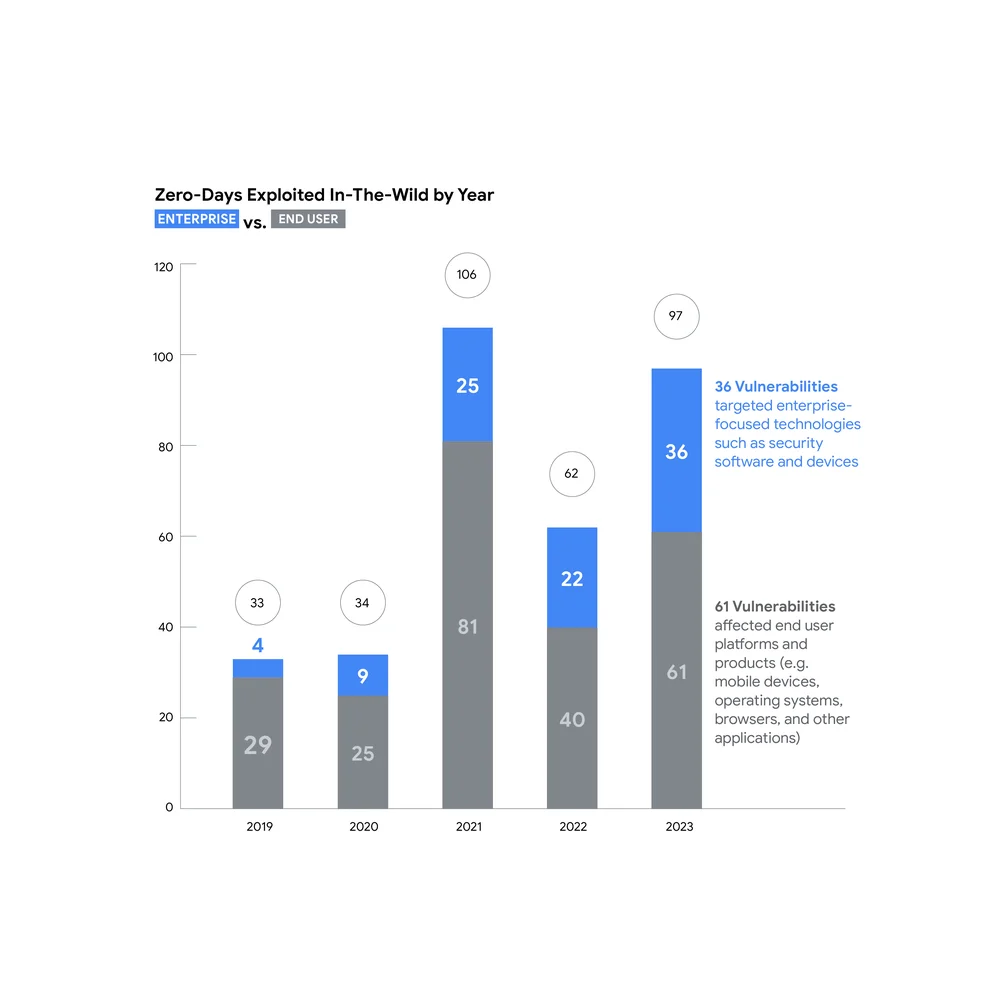
Zero-Day Exploits: The Race Against Time to Secure Vulnerabilities
A zero-day exploit is a cyber-attack that occurs on the same day a weakness is discovered in software. This happens before the software creators have a chance to issue a fix, making it a race against time to secure vulnerabilities.
Understanding zero-day exploits is essential for IT managers and business owners. It underscores the need for continuous monitoring of IT systems and prompt response to identified vulnerabilities. Awareness of this term can guide the development of incident response plans and the adoption of proactive security measures.
What are the cybersecurity terms to describe insider threats?
Some common cybersecurity terms used to describe insider threats include:
1. Insider Threat: This refers to any individual within an organization who poses a threat to the security of the company’s data, systems, or network. This could be due to malicious intent, negligence, or simply being unaware of security best practices.
2. Privileged Insider: A privileged insider is someone within the organization who has access to sensitive information or critical systems due to their role or level of access. This type of insider threat can be particularly dangerous as they have the potential to cause significant damage.
3. Insider Attack: An insider attack occurs when a trusted individual within the organization intentionally or unintentionally compromises the security of the company’s systems or data. This could involve stealing data, installing malware, or sabotaging systems.
4. Insider Risk: Insider risk refers to the potential threat that insiders pose to an organization’s cybersecurity. This includes the risk of data breaches, financial loss, reputational damage, and legal consequences.
5. Insider Monitoring: Insider monitoring involves the use of tools and technologies to track and analyze the behavior of insiders within the organization. This can help detect suspicious activities and prevent insider threats before they cause harm.
What does the term exploit mean in cybersecurity?
An “exploit” in cybersecurity is a tool that takes advantage of a weakness in a computer system or application. This tool can be software, data, or commands. It is used to gain unauthorized access or cause harm to the system. Cyber attackers use exploits to get into a system without permission and do harmful things like running malicious code.
These vulnerabilities may exist due to programming errors, misconfigurations, or other weaknesses in the system’s defenses. By exploiting these vulnerabilities, attackers can bypass security measures and compromise the confidentiality, integrity, or availability of the targeted system or data. Organizations need to update their systems and applications regularly to stop bad actors from taking advantage of known weaknesses.
Conclusion: The Imperative of Cybersecurity Awareness
In the digital age, understanding cybersecurity terms is not just a necessity for IT professionals, but for everyone. It empowers individuals and organizations to protect their digital assets effectively. By familiarizing ourselves with these terms, we can better navigate the digital landscape, ensuring the security and success of our businesses.